Is your computer free of all
Trojans ?
This page contains:
1) Comments on checking for trojans in your computer,
2) Short review of the free utility StartUp.CPL,
3) Comments on the DOS-Window console command netstat
.
The first defense against trojans (or viruses)
is to practice "safe computing." (See my page on
How To Keep Viruses/Trojans Out of Your Computer.)
Sooner or later, those who quickly execute programs coming from
unreliable sources will get hit with a trojan or virus or even a number of
them all at once! ( If someone finds an open door into your computer, they
might dump a bunch of their own trojans/viruses on it before you remove the generic
one that gave them first access!)
A very important exercise, especially for
those at risk, is to spend some time getting to know as much as you
can about the programs which are "automatically" run by your
computer at boot-up:
Try looking at your START -> Programs -> StartUp menu
listings first to get an idea of what we're describing here: programs that
start without you having to click on them. ( The shortcut links are actually
stored in your
C:\WINDOWS\Start Menu\Programs\Start Up folder.)
Your next step might be: discovering if there are any programs started by
your computer's WIN.INI file. Search for the file in your
WINDOWS folder. If you find WIN.INI, make a copy of the file;
call it WININI.TXT for example.
Open the copy with any text editor such as Notepad. See if there are
any programs started by the file's "run =
" or "load =
" lines! ( On most Win OS installations today, there won't be
any. If there is one, try to learn what the command does and which
application put it there.)
Here's the beginning of my own WIN.INI
file (no commands in mine!):
[windows]
load=
run=
NullPort=None
device=
The major locations which trojans use
to make sure they 're always running on a computer are within the REGISTRY. You can download a
batch file I've written that will list programs that are started by
your Registry at boot-up:
REGCheck (click here for more details);
this is a "safe" read-only program which does not allow
you to make any changes to your Registry...
or you can get another program which can make changes to your Registry:
Startup.CPL (for Win
95/98/NT/2000)
This program conveniently lists all the locations
in your Registry and the StartUp folder where trojan executions may be trying
to hide. It's still up to you though to identify which programs are the
trojan servers (or others you may simply not want running)!
After you've downloaded and run the installation file (StartupCPL.exe),
you'll find the program itself in your Control Panel as "Startup"
(place a shortcut on your Desktop if you want to get to it more quickly).
[Note: There's a stand-alone version too!] The program is registered in your
"Add/Remove Programs Properties" so you can easily uninstall it
if you wish. ( I've been using Startup for many months now and never had a
problem with it.)

'What's the
"Deleted" tab for?' you ask: Well this is where you'll find keys
that you've removed; kinda like a recycle bin for startup keys! They won't
run at system startup, but will still be stored here should you ever want
to use them again. To permanently remove a key or program, simply delete it
from the Deleted tab window.
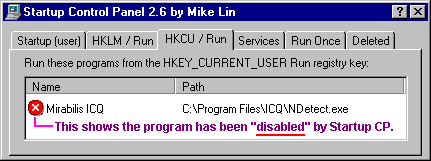
So, where are the 'disabled' keys stored? They are kept in Mike's software
key at:
[ HKEY_CURRENT_USER\Software\mlin\StartupCPL\Disabled ].
Note: If you have Win 98/NT/2000, you'll probably really appreciate Mike's
new utility StartUp Monitor. ( Since it doesn't work with Win 95,
the OS I run at home, it isn't possible for me to review it here!)
There's a very easy step you can take to check for trojans
running on your system. Check for a "virtual port" that is always
open by using this console command: netstat -a at a
command prompt in a DOS-Window. (The
-a parameter will show UDP connections in addition to the TCP
connections; even if they are still 'listening' without an active
connection. This is great for checking to see if a trojan is running before
you go online!) For example, if you are either infected with the old BO
trojan server set to listen on the default port (31337), or you have
installed and are running the BoSpy program,
then your screen will look like this even before you are
connected to the Internet:
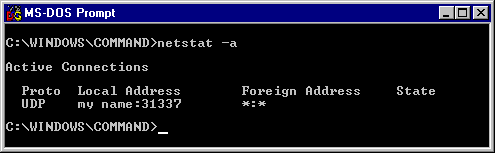
The
phrase "my name" in the screen pic above will be the name of your
computer. If you use the command netstat -an, then you'll see either
0.0.0.0 or 127.0.0.1 here instead of your computer name. For
more about the netstat and other Network commands, see my page:
MS-DOS 7 Internet Programs.
 Back
to The Starman's BO Trojan page.
Back
to The Starman's BO Trojan page.



